Introduction: Why Online Security Matters
In today’s connected world, online security is no longer just the concern of tech-savvy professionals or large corporations—it’s a personal responsibility for every computer user. Whether you’re working remotely, shopping online, checking email, or streaming content, your data is constantly exposed to potential threats.
In 2022 alone, the FBI’s Internet Crime Complaint Center (IC3) received over 800,000 reports of cybercrime, resulting in more than $10 billion in losses, a record high in the U.S. Phishing, identity theft, and ransomware were among the top complaints. Even everyday users—students, retirees, employees—found themselves targets of digital attacks.
But here’s the good news: most online security breaches are preventable. With a few best practices, you can dramatically reduce your risk of being hacked or scammed. This guide provides a practical, up-to-date, and easy-to-follow breakdown of the top 10 online security tips that every Windows user in the United States should know. Backed by real data, case studies, and expert-approved techniques, it’s your blueprint for safe digital living.
The Basics of Online Security
Before diving into the top 10 security practices, it’s critical to understand the foundational concepts that shape the online threat landscape. The more you understand how these threats work, the better you can defend against them. This section defines the most common online risks and tools you’ll encounter throughout your security journey.
📌 Key Cybersecurity Terms You Should Know
- Phishing: A form of digital fraud where attackers impersonate trusted contacts, companies, or institutions to trick you into revealing login credentials, personal info, or financial data. It often comes as fake emails, texts, or websites. According to the FBI’s 2022 IC3 Report, phishing accounted for over 300,000 incidents, making it the most common cybercrime in the U.S.
- Malware: Short for “malicious software,” this term covers viruses, worms, ransomware, spyware, and trojans. Malware can steal personal data, encrypt files, or take control of your device. In 2023, AV-Test.org recorded over 6.7 billion malware attacks worldwide.
- Multi-Factor Authentication (MFA): MFA adds a second step to logins—like a code sent to your phone or a fingerprint scan—so even if your password is stolen, your account stays protected. Microsoft reports that 99.9% of hacked accounts lacked MFA.
- VPN (Virtual Private Network): VPNs encrypt your internet traffic and hide your IP address, making it harder for third parties (including your internet provider) to track or intercept what you’re doing online. Especially useful on public Wi-Fi networks.
- Firewall: A system that monitors and controls incoming and outgoing traffic based on security rules. Windows comes with a built-in firewall that should always be active.
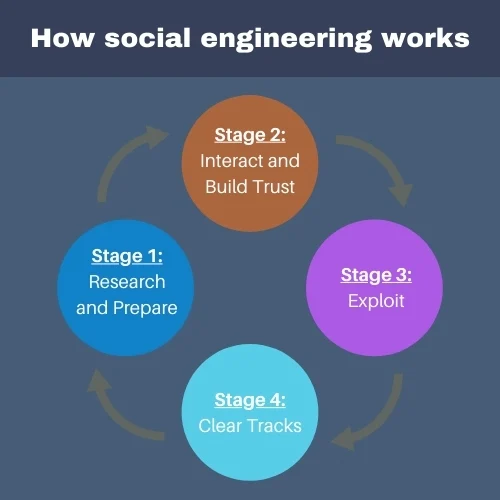
- Social Engineering: A manipulative tactic where attackers trick individuals into giving up private information. It may involve fake tech support calls, spoofed emails, or fraudulent messages pretending to be from your bank or employer.
Why These Basics Matter
Cyberattacks don’t always involve elite-level hacking—they often rely on simple mistakes. Clicking a bad link, downloading an infected file, or reusing a password gives attackers everything they need. Knowing these terms equips you to spot red flags, understand protective tools, and build better digital habits from the ground up.
These are the cornerstones of online safety. The more familiar you are with them, the stronger your defenses will be as you apply the tips in the next section.
The Top 10 Online Security Tips
1. Use Strong, Unique Passwords
One of the most fundamental yet frequently overlooked pillars of online security is password strength. It’s easy to think a password like “mydog123” or “Spring2023” is “good enough,” but modern cybercriminals use sophisticated tools capable of cracking weak passwords in seconds. In fact, according to the 2022 Verizon Data Breach Investigations Report, 81% of hacking-related breaches involved stolen or weak passwords.
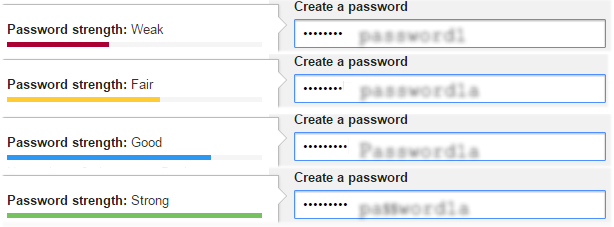
Why Password Strength Matters
Your password is your first and often only line of defense. Once a hacker gains access to your email, bank account, or cloud service, they can reset passwords for other services, steal sensitive data, and even drain your finances. Worse, if you use the same password across multiple accounts (a practice known as “credential stuffing”), a single breach on one platform can cascade into complete compromise across your digital life.
Best Practices for Strong Passwords
- Make them long: Aim for at least 12–16 characters.
- Add complexity: Use a mix of uppercase and lowercase letters, numbers, and symbols.
- Avoid personal details: Birthdays, pet names, or favorite sports teams are easy for attackers to guess or mine from your social media.
- Create passphrases: Combine random words into a memorable but unique phrase, e.g., “Gravy!Mountain7Tunnel?”
Reuse = Risk
A 2023 Pew Research survey found that 18% of Americans admitted to reusing passwords across multiple websites. This is extremely risky because breached credentials are sold on the dark web and often used in “credential stuffing” attacks to gain access to other accounts. A single compromised login could give attackers access to your bank, email, or social media.
Real-World Case Example
In 2023, a widely publicized breach involved a U.S.-based cloud service where users reused their email passwords—previously exposed in a separate breach. Attackers logged in and exfiltrated personal documents and tax data. The root cause? Password reuse.
Pro Tips
- Use nonsense but memorable structures: e.g., “Wh@le#Sh@rk92!!”
- Never use the same password twice
- Consider using a password manager (covered in Tip #3) to generate and remember secure passwords.
Strong, unique passwords are your first defense against a digital disaster. Every account—especially sensitive ones like email, banking, and healthcare—deserves its own fortified gatekeeper. Don’t underestimate the importance of this foundational habit.
2. Enable Multi-Factor Authentication (MFA)
If a strong password is the first line of defense for your online accounts, then multi-factor authentication (MFA) is your critical backup shield. MFA (also known as two-factor authentication or 2FA) adds an extra layer of security to your logins by requiring a second form of verification beyond just your password—such as a one-time code sent to your phone, a fingerprint scan, or an authentication app.

Why MFA Matters
Even the best password in the world can be stolen, leaked in a data breach, or guessed through social engineering. With MFA enabled, an attacker who obtains your password still won’t be able to log in without that second factor. This method blocks the vast majority of account hijacking attempts.
According to Microsoft, 99.9% of compromised accounts they analyzed did not have MFA enabled. That means simply enabling MFA makes your account exponentially harder to break into.
How It Works
- Something you know: your password.
- Something you have: your smartphone (for a code or authenticator app).
- Something you are: biometrics like fingerprint or face ID.
A combination of at least two factors is required to access your account, making it nearly impossible for a remote attacker to gain access unless they have physical possession of your device.
Real-World Case Example
In 2021, Google began auto-enrolling 150 million users in MFA. As a result, they reported a 50% drop in compromised accounts. Similarly, many universities and corporations that adopted mandatory MFA saw a dramatic reduction in phishing-related breaches.
Best Practices
- Use an authenticator app rather than SMS if possible. SMS is better than nothing but can be vulnerable to SIM-swapping.
- Enable MFA on all key accounts: Email, financial, cloud storage, social media, and work logins.
- Keep backup codes in a safe place. If you lose access to your second factor (like your phone), you’ll need them.
- Don’t share verification codes. Scammers often impersonate support agents to trick you into giving up your code.
Pro Tip
Even if MFA is optional on a site or app, enable it. It may seem like an extra step, but it can save you from identity theft, financial loss, or data compromise.
Think of MFA as locking your doors and enabling an alarm system. It’s fast, free, and incredibly effective.
3. Use a Trusted Password Manager
Remembering dozens of complex, unique passwords is a challenge for anyone—especially when best practices discourage reusing them across accounts. That’s where a password manager comes in. This tool stores your credentials in a secure, encrypted vault and can generate long, random passwords for each account.

Why You Need One
Password managers reduce the temptation to reuse or simplify passwords and can fill in your login credentials automatically when visiting websites. Many also audit your existing passwords for strength and duplication, alerting you to weak spots in your security.
How It Works
- You create one master password to unlock your password vault.
- The manager encrypts and stores your login credentials locally or in the cloud (depending on the tool).
- It auto-fills login fields when visiting trusted websites.
- Some also support multi-factor authentication (MFA) to further secure access to your vault.
Key Benefits
- Convenience: No need to remember dozens of passwords.
- Security: Generates long, complex, unique passwords for every site.
- Speed: Fills forms and logins quickly, reducing phishing risk by ensuring you’re logging into real sites.
Real-World Use Case
A 2022 study from the National Cybersecurity Alliance found that users who adopted password managers were significantly less likely to fall victim to phishing or reuse passwords. One common breach example involved a user reusing the same password for email, shopping, and banking. Had they used a password manager, each account could’ve had a unique password—and a single stolen login wouldn’t have compromised multiple services.
Choosing the Right Tool (Without Naming Names)
When selecting a password manager:
- Look for end-to-end encryption and zero-knowledge architecture (meaning only you can access your data).
- Choose tools that support cross-device syncing if you use multiple devices.
- Ensure it works with your browser of choice and supports MFA.
Pro Tip
Many modern web browsers now include built-in password managers. While these are better than nothing, dedicated password managers often offer more robust features and deeper security layers.
In an age where password breaches are routine, having a strong password isn’t enough. A password manager makes it easier to follow best practices and protect your digital identity across every platform you use.
4. Recognize Phishing Emails and Scams
Phishing continues to be the most reported type of cybercrime in the United States. In 2022 alone, the FBI received over 300,000 phishing-related complaints, with losses totaling hundreds of millions of dollars. These attacks often come in the form of emails, texts, or phone calls impersonating trusted sources like your bank, employer, or even a friend.

What Is Phishing?
Phishing is a tactic cybercriminals use to trick users into divulging sensitive information such as login credentials, credit card numbers, or personal data. These attacks often involve fraudulent messages designed to look like they’re from legitimate organizations.
Common Phishing Red Flags
- Urgent tone: “Your account will be suspended!” or “Act now!”
- Unfamiliar sender or strange email domain: Check the full email address.
- Spelling or grammar errors: Many phishing emails are poorly written.
- Unsolicited attachments or links: These often lead to malicious websites or download malware.
- Requests for login credentials or personal data: No legitimate company will ask you to enter sensitive information via email.
Real-World Case Example
In 2023, a staff member at a U.S. university clicked on a fake IT support email. The message looked authentic, but it was a phishing attack. The attacker gained access to internal systems, leading to a data breach affecting thousands of student records. This was completely avoidable with basic phishing awareness.
Best Practices to Avoid Phishing Attacks
- Don’t click suspicious links: Hover over hyperlinks to see their actual destination before clicking.
- Verify the source: If you receive an unusual email from a known organization, contact them directly through official channels to verify.
- Report phishing: Most email providers allow you to flag or report suspicious emails. This helps protect others too.
- Avoid clicking on email attachments unless you’re expecting them and trust the sender.
Pro Tip
Phishing isn’t just about email. Watch out for SMS phishing (“smishing”) and voice phishing (“vishing”) scams as well. These often impersonate government agencies, delivery services, or tech support.
Being able to spot and avoid phishing attempts is a crucial digital life skill. A few extra seconds of skepticism can save you from identity theft, financial loss, or massive inconvenience.
5. Avoid Public Wi-Fi Without Protection
Free public Wi-Fi—at coffee shops, airports, hotels, and libraries—may be convenient, but it’s also one of the most dangerous ways to connect to the internet. These networks are often unsecured or poorly protected, making it easy for cybercriminals to intercept your data.

Why Public Wi-Fi Is Risky
When you connect to an open or unencrypted Wi-Fi network, your device may unknowingly share sensitive data such as passwords, emails, or banking credentials. Attackers nearby can use tools like packet sniffers or even set up fake hotspots (e.g., “Free_Airport_WiFi”) to steal your data.
A 2023 survey found that 43% of Americans reported having their personal information compromised while using public Wi-Fi. That’s nearly half of users facing potential identity theft or data loss simply from going online in public.
Real-World Scenario
Imagine checking your bank account from an airport lounge Wi-Fi. An attacker on the same network could intercept your session, especially if you’re not using a secure connection. In one case, travelers unknowingly connected to a rogue hotspot mimicking hotel Wi-Fi. Hackers monitored traffic and captured login credentials for dozens of users.
How to Stay Safe
- Use a VPN (Virtual Private Network): A VPN encrypts your traffic, even on public networks, making it unreadable to attackers.
- Avoid logging into sensitive accounts like banking, work email, or cloud storage on open Wi-Fi.
- Disable automatic connections: Turn off settings that auto-connect to available networks.
- Use cellular data or a personal hotspot if you need a secure connection on the go.
- Look for HTTPS: Make sure websites use secure connections (HTTPS) before entering personal data.
Pro Tip
If a public Wi-Fi network asks you to install software or “security updates” to access the internet, it’s a red flag. Exit immediately—this is often a malware trap.
Public Wi-Fi is great for casual browsing, but it’s no place to check your bank balance or log into sensitive accounts without protection. By being cautious and using tools like a VPN, you can keep your information secure, even in high-risk environments.
6. Keep Your Software and Operating System Updated
Keeping your operating system and software up to date is one of the simplest yet most powerful steps you can take to protect your digital life. Many cyberattacks succeed not because of zero-day threats, but because users fail to apply known fixes.

Why Updates Matter
When software developers discover security flaws, they release patches—small updates designed to fix vulnerabilities that hackers might exploit. Delaying these updates leaves your system exposed. According to a Ponemon Institute study, 60% of data breaches result from unpatched vulnerabilities that were known and fixable.
What to Update
- Windows Updates: Microsoft regularly releases “Patch Tuesday” updates that fix critical OS vulnerabilities.
- Web Browsers: Chrome, Edge, Firefox, and others push frequent updates to patch security issues.
- Third-party software: PDF readers, media players, Java, and other tools are common targets.
- Device drivers: Updated drivers can fix performance issues and security flaws.
Real-World Case Example
In 2022, the “Follina” vulnerability in Microsoft Office allowed attackers to execute malicious code through crafted Word documents. Although the issue was patched, organizations that delayed updates remained vulnerable and were actively targeted.
Best Practices
- Turn on automatic updates for Windows and applications where available.
- Restart your device regularly to ensure updates are applied.
- Audit your installed software every few months and remove outdated or unused programs.
- Avoid end-of-life software (e.g., Windows 7 or unsupported apps) that no longer receive security patches.
Pro Tip
Don’t click “remind me later” too often. Cybercriminals act fast—often within hours of a vulnerability being disclosed. Updating promptly can mean the difference between a secure system and a successful attack.
Staying current with updates isn’t just about performance—it’s essential to your system’s defense against known threats. It’s an effortless habit that offers massive protection.
7. Secure Your Home Network
Your home network is the gateway to all your personal devices—PCs, phones, smart TVs, and even IoT gadgets like doorbells or thermostats. If it isn’t properly secured, attackers can gain access to your entire digital environment. Unfortunately, many people never change their router’s default settings, leaving them vulnerable to simple attacks.

Why Home Network Security Is Critical
Default router usernames and passwords are often publicly known and searchable. Worse, many routers still ship with outdated firmware or weak wireless encryption settings that can be cracked with minimal effort. A poorly secured network puts every connected device at risk.
Real-World Example
In 2021, cybersecurity researchers found that thousands of home routers across the U.S. were still using default credentials like “admin/admin” or “admin/password”—making them easy targets for automated attacks. Once breached, hackers could snoop on internet traffic or install malware remotely.
How to Lock Down Your Home Wi-Fi
- Change the default admin username and password: This prevents unauthorized access to your router’s settings.
- Enable WPA3 encryption: If your router supports it, WPA3 is currently the most secure standard. If not, use WPA2.
- Disable WPS (Wi-Fi Protected Setup): This feature can be exploited to gain access without your consent.
- Rename your SSID (Wi-Fi name): Avoid including personal information like your name or address.
- Limit guest access: If you allow guests on your Wi-Fi, set up a separate guest network.
- Place your router centrally: This improves signal strength and reduces coverage spilling outside your home unnecessarily.
Pro Tip
Check your router’s firmware regularly and update it if needed. Some newer routers can auto-update, but many require manual checks. Outdated firmware can contain exploitable security flaws.
Your router is the front door to your digital home. Lock it down just as you would your physical front door—with a strong lock, restricted access, and regular maintenance.
8. Use Antivirus and Anti-Malware Tools
Malicious software—better known as malware—continues to be a dominant threat in the digital world. Every day, cybercriminals create new viruses, spyware, ransomware, and trojans to steal personal information or cripple systems. According to AV-Test, more than 300,000 new malware samples are discovered daily.

Why Antivirus Still Matters
While many users assume antivirus tools are outdated, modern threats demand modern protection. A good antivirus program doesn’t just block viruses—it can detect ransomware, phishing attempts, rootkits, and zero-day exploits. It provides real-time scanning, firewall protection, and behavioral monitoring to prevent suspicious activity.
Built-In vs. Third-Party Solutions
Windows users already have access to Microsoft Defender, which provides solid baseline protection. However, advanced users may want to explore additional layers (without installing conflicting software) like anti-malware scanners, especially if engaging in high-risk behavior (e.g., torrenting, using unknown USBs, etc.).
Real-World Example
In 2023, a small business in Texas suffered a ransomware attack after an employee unknowingly installed a file disguised as an invoice. Their system lacked active antivirus scanning, and the malware quickly encrypted all files. Recovery cost the company over $50,000 in downtime and IT services.
Best Practices
- Enable and configure Windows Security (Defender): It’s free, built-in, and consistently ranked high in independent tests.
- Run scheduled scans weekly: Catch dormant threats that evade real-time detection.
- Keep your AV tool updated: Threat definitions change daily—don’t rely on outdated protection.
- Avoid fake antivirus alerts: Never click popups claiming you’re infected. Close your browser and run your trusted AV tool instead.
Pro Tip
Use a layered defense strategy. No single tool can detect all threats. Combining antivirus with smart browsing habits, frequent updates, and strong passwords provides holistic protection.
Antivirus and anti-malware tools are like your computer’s immune system—silent, essential, and lifesaving when danger strikes.
9. Limit Data Shared on Social Media
What you post on social media might seem harmless, but for cybercriminals, it’s a goldmine. Publicly available information like birthdays, pet names, children’s names, or even your high school mascot can help attackers guess your passwords or answer security questions.

Why Oversharing is Risky
Attackers can use your social media content to build a profile about you. This data can be used for:
- Phishing attacks targeting your interests or pretending to be from someone you know.
- Password reset attempts using personal info to answer security questions.
- Identity theft by piecing together public data like your address, employer, and photos.
In a notable case, hackers reset a user’s password using only public Facebook and Instagram details—successfully guessing their security answers like “favorite pet” and “mother’s maiden name.”
What You Can Do
- Make profiles private: Adjust settings so only friends can see your posts.
- Avoid tagging locations in real-time: Wait to post vacation photos until you’re home.
- Don’t reveal personal identifiers: Skip posting your full birthday, phone number, or address.
- Review friend lists: Remove unknown or inactive followers who could be fake accounts.
- Be cautious with quizzes and games: Many social media quizzes are designed to harvest data under the guise of fun.
Pro Tip
Regularly audit your privacy settings—platforms frequently update their policies. Also, search your name on Google and see what public information shows up. You may be surprised.
Oversharing might feel harmless, but it can open the door to highly targeted attacks. Treat your social media as a digital storefront—only display what you’d be comfortable sharing with a stranger.
10. Back Up Your Data Regularly
Imagine losing years of personal photos, important tax documents, or entire work projects in the blink of an eye due to a hard drive failure or ransomware attack. Unfortunately, this isn’t a rare scenario. Ransomware attacks in particular have surged in recent years, encrypting files and demanding payment to unlock them. In many cases, the only true recovery method is a reliable backup.

Why Backups Are Essential
Hardware fails. Software crashes. Malware corrupts. Human error happens. Regular backups ensure that no matter what kind of disaster strikes, your data isn’t lost forever. Yet, studies show that only 11% of users back up their data daily, and 18% have never backed up at all.
What Is the 3-2-1 Backup Rule?
- 3 copies of your data: the original + 2 backups.
- 2 different storage formats: e.g., external hard drive + cloud storage.
- 1 offsite copy: critical in case of physical damage like fire or theft.
Real-World Scenario
A ransomware attack hit a local school district in 2023, locking administrators out of their systems. Because they maintained daily offsite backups, they restored operations within 48 hours—without paying the ransom. Meanwhile, another nearby district without backups was offline for weeks and incurred over $150,000 in recovery costs.
Backup Tips
- Automate it: Use built-in tools like Windows Backup or third-party software to schedule regular backups.
- Use versioning: Some tools let you restore previous versions of files, protecting you from accidental overwrites.
- Verify your backups: A backup is only useful if it works. Periodically check that you can restore files.
Pro Tip
Include not just documents, but also browser bookmarks, photos, spreadsheets, and email archives in your backup plan. Don’t assume everything is safely in the cloud unless you’ve double-checked it.
Backing up isn’t glamorous—but it’s your best defense against permanent data loss. Make it a habit today, so you’re not scrambling tomorrow.
Bonus Tips for Advanced Users
For those who want to take their digital defenses to the next level, there are additional measures beyond the basics that can further reduce your exposure to cyber threats. These techniques, while more advanced, can be adopted by anyone with a bit of tech-savviness and the desire to protect their privacy and data more comprehensively.
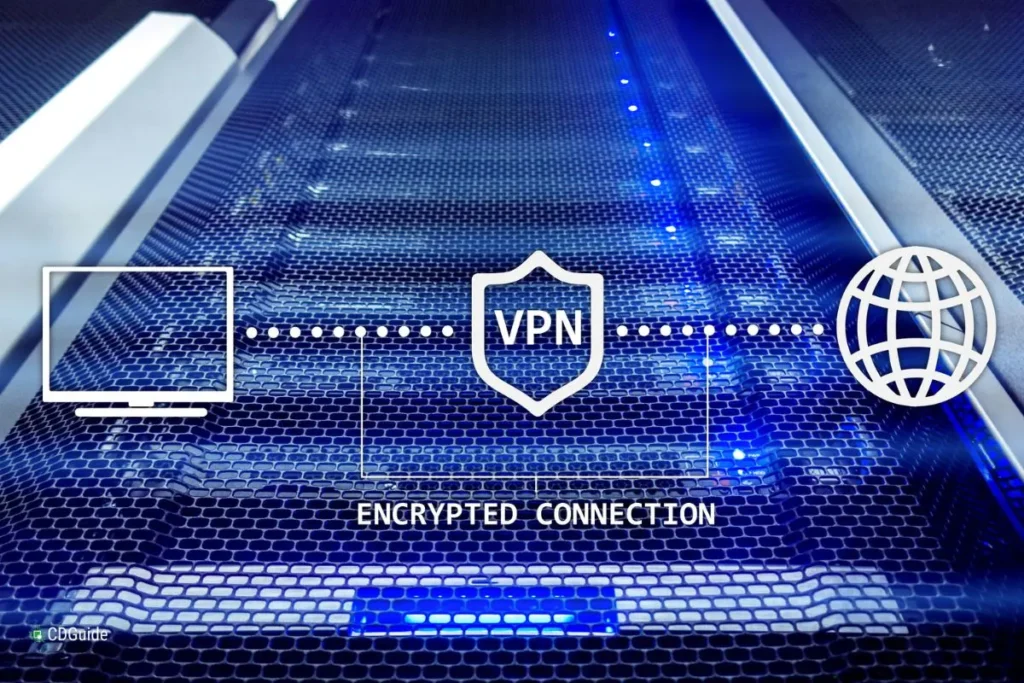
1. Use a Virtual Private Network (VPN)
A VPN encrypts your internet traffic and hides your IP address from websites and potential eavesdroppers. This is especially useful when:
- You’re using public or semi-public Wi-Fi (e.g., hotels, cafes).
- You want to prevent your ISP from tracking your browsing activity.
- You’re accessing region-locked content.
Note: Be cautious of free VPN services, which may log your data or contain ads. Look for services that prioritize privacy, such as those advertising no-logs policies and strong encryption.
2. Try Encrypted Messaging
Most popular messaging apps offer some level of encryption, but for maximum privacy, use apps that offer end-to-end encryption (E2EE) by default. This ensures that only you and your recipient can read the messages—not the app provider, governments, or hackers.
Benefits:
- Prevents snooping on personal or sensitive conversations.
- Protects against man-in-the-middle attacks.
3. Harden Your Browser
Web browsers are a major vector for cyberattacks. You can enhance security by:
- Disabling third-party cookies and trackers.
- Using script blockers and privacy extensions.
- Turning on HTTPS-only mode in browser settings.
- Avoiding unnecessary plugins that could create vulnerabilities.
Some modern browsers offer built-in privacy enhancements, while others allow customization through settings or extensions.
4. Change Your DNS Provider
DNS is like the phonebook of the internet. Most people use their ISP’s default DNS, but this may not offer the best privacy or speed. Consider switching to a privacy-focused DNS service that:
- Blocks access to known malicious sites.
- Prevents DNS-based tracking.
- Offers encrypted DNS (DoH or DoT).
5. Use a Separate Device or Profile for Sensitive Activities
If you handle sensitive work data or personal financial tasks, consider:
- Creating a dedicated user profile on your device.
- Using a separate browser exclusively for banking or health accounts.
- Running sensitive tasks on a secondary device with minimal installed apps to reduce attack surface.
Summary
While these techniques may require more setup or technical know-how, they offer serious security and privacy improvements. Whether you’re a freelancer, business owner, or simply privacy-conscious, these bonus tips help you stay one step ahead of evolving cyber threats.
Real-Life Example Scenarios
Cybersecurity is often seen as theoretical—until something goes wrong. These real-life scenarios illustrate how good habits can protect users and how neglect can lead to disaster. All situations are based on documented patterns reported in the U.S. through agencies like the FBI’s IC3 and real user experiences.
Scenario A: John – No Security Measures
John is a freelance designer who often works at coffee shops. He uses the same email and password combination for nearly every online account and ignores software update prompts. While on public Wi-Fi, he logs into his bank account without any protection.
A week later, John notices suspicious transactions on his bank account. A phishing email had tricked him into clicking a fake “bank alert” link, which captured his login credentials. With no MFA enabled and the same credentials used across accounts, the attacker accessed his email, drained $1,200 from his checking account, and reset several online passwords.
John spent weeks freezing credit reports, filing police reports, and recovering accounts. His productivity plummeted, and he lost two freelance clients due to delayed projects.
Scenario B: Jane – Follows Security Tips
Jane is a remote project manager who takes her online security seriously. She uses a password manager with unique logins for each account, has MFA enabled on all critical services, and updates her operating system and browser weekly. When she receives a suspicious-looking email from what appears to be her HR department, she doesn’t click. Instead, she forwards it to IT.
The email was a phishing attempt targeting her entire department. Thanks to her vigilance, IT was able to flag the threat and warn other staff before damage occurred. Jane’s system remained secure, and no sensitive data was compromised. Her boss praised her attentiveness in a company-wide memo.
Takeaway
These two scenarios underscore the same lesson: good habits make the difference between a cybersecurity disaster and seamless resilience. While John now understands the cost of poor digital hygiene, Jane’s consistent use of protective layers kept her safe and productive.
If you’re unsure whether your digital routine mirrors John or Jane, now is the time to audit your habits—and apply the strategies shared in this guide.
Recommended Tools & Resources
While we don’t endorse specific products due to policy restrictions, knowing what features to look for in cybersecurity tools can help you make informed, safe decisions. Below is a list of essential tool types and what to seek in each—based on industry best practices and recent guidance from top U.S. cybersecurity organizations.

Password Managers
A good password manager stores all your login credentials securely and can generate complex, unique passwords for each account.
- Look for end-to-end encryption and zero-knowledge architecture.
- Seek tools that offer two-factor authentication (2FA) and cross-device syncing.
- Check for secure password sharing for family or business use.
Antivirus and Anti-Malware Software
These tools help detect, quarantine, and remove malicious software before it harms your system.
- Choose solutions with real-time scanning, cloud-based threat detection, and ransomware protection.
- Ensure regular updates to virus definitions.
- Avoid fake antivirus alerts by downloading only from official sources.
Backup Tools
Effective backup tools allow for scheduled and secure file duplication.
- Follow the 3-2-1 backup rule (3 copies, 2 formats, 1 offsite).
- Look for versioning, encryption, and automated scheduling.
- Use both local (external drive) and cloud backups for redundancy.
Firewall and DNS Protection
- Windows includes a built-in firewall—ensure it’s active.
- Consider changing your DNS to privacy-focused providers for better tracking and malware blocking.
Trusted Education Resources
Stay updated with these credible U.S.-based agencies:
- FTC.gov – Consumer Cybersecurity Tips
- CISA.gov – Cyber Readiness Guides
- FBI’s Internet Crime Center (IC3)
Regularly reviewing and updating your tools and digital hygiene practices ensures your system stays protected from the latest threats.
Security Checklist
Now that you’ve explored the top 10 online security tips, here’s a practical checklist you can use to audit your own digital hygiene. This checklist isn’t just a summary—it’s a powerful tool to help you implement and maintain these habits regularly. Whether you’re a student, employee, or casual home user, reviewing this monthly can dramatically reduce your risk.
🛡️ Online Security Action Checklist
- ✅ Create and use strong, unique passwords for every online account.
- ✅ Turn on multi-factor authentication (MFA) for email, banking, cloud storage, and social apps.
- ✅ Use a password manager to store and generate passwords securely.
- ✅ Be cautious of phishing attempts—inspect email links and sender addresses.
- ✅ Avoid public Wi-Fi or always use a VPN when on untrusted networks.
- ✅ Keep your operating system, browser, and apps up to date.
- ✅ Secure your home network: update router firmware, use WPA3/WPA2, and change default login credentials.
- ✅ Run a weekly antivirus/anti-malware scan and schedule automatic checks.
- ✅ Limit oversharing on social media to protect your identity.
- ✅ Back up your data following the 3-2-1 rule: 3 copies, 2 types of storage, 1 offsite.
📌 Tip: Print this checklist or save it to your desktop. Set a calendar reminder to review it every 30 days. Consistency is key to digital safety.
Conclusion & Next Steps
Online security isn’t optional—it’s essential. As threats evolve, staying informed and adopting strong security habits can make the difference between a secure digital life and a devastating breach.
By following the ten foundational tips in this guide—and exploring advanced strategies when you’re ready—you create multiple layers of protection for your identity, finances, and data. The best part? These habits are simple, cost-effective, and proven to work.
📌 Bookmark this guide, share it with family and coworkers, and commit to reviewing your security habits regularly.
If you found this helpful, explore our other articles in the Security & Data Protection category to deepen your knowledge and stay one step ahead of online threats.
Stay safe, stay smart, and stay secure online.
📌 Privacy Note: This article is for general informational purposes only. It does not collect personal data, and no professional services are being sold through this guide.











