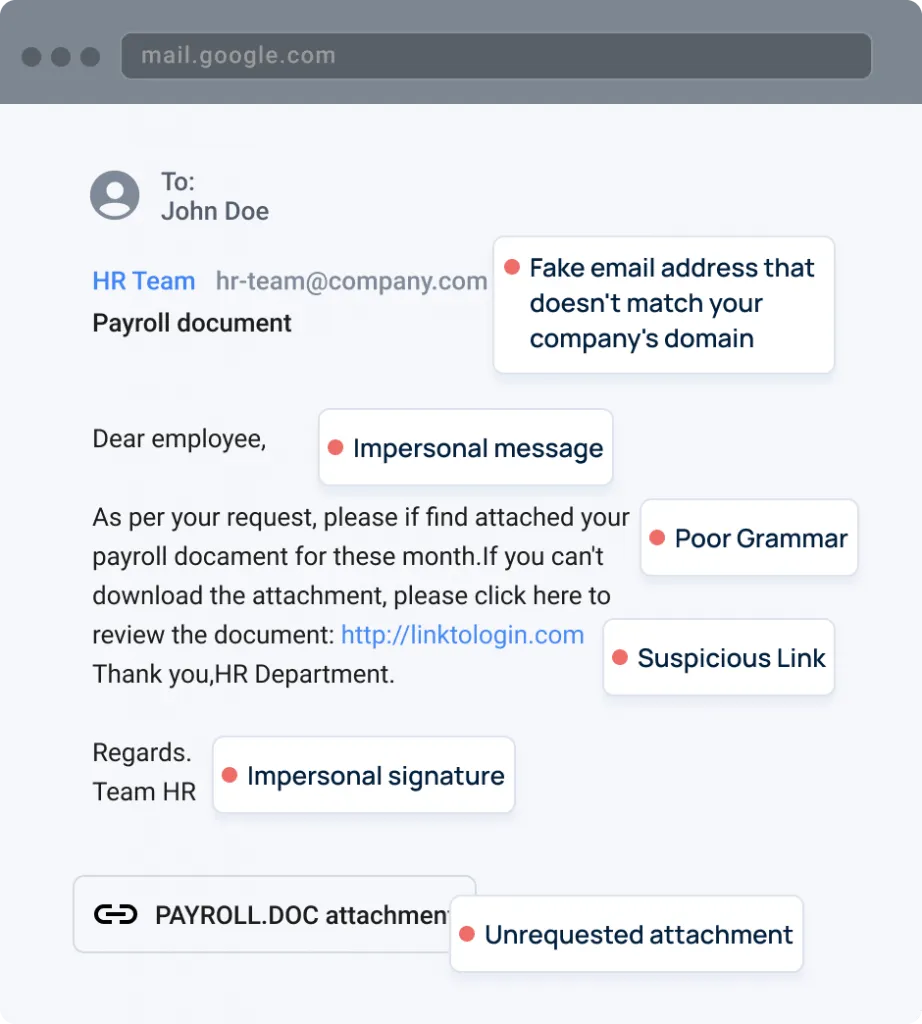
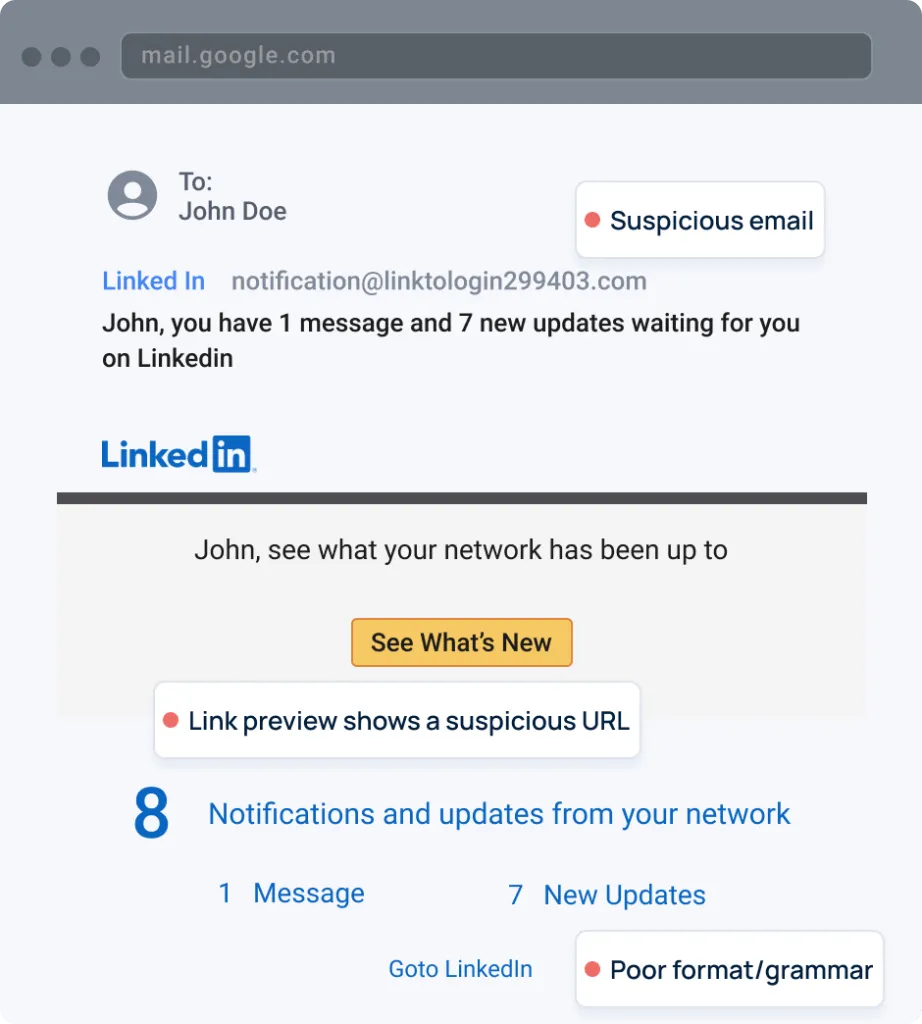
Phishing is a form of social engineering cyberattack where cybercriminals pretend to be a genuine company or person through a deceptive email, aiming to steal sensitive information or infect the user’s device with malware.
Examples of phishing emails can be quite helpful in recognizing and understanding the real dangers that exist. Malicious messages are designed to mimic genuine emails. Many of them require immediate attention, such as resetting passwords or confirming personal data. Some even come with unexpected attachments. On the other hand, it can be quite challenging to detect highly targeted phishing attacks.
Ensuring the safety of your employees from phishing attacks involves providing them with valuable knowledge about the various forms of malicious emails. In addition, it is important to provide guidance to your team members on how to carefully examine the structure of each email in order to identify any potential signs of suspicious activity.
Here are some examples of phishing emails that can help you navigate through them.
Exploring the Anatomy of a Phishing Email
Before we present a few examples of phishing emails, let’s go over some data: A recent survey by GreatHorn reveals a worrying trend: users consistently miss almost 50% of phishing attacks. This occurs due to a lack of cybersecurity awareness among employees, coupled with the cunning tactics employed by cybercriminals who craft highly personalized emails that closely mimic legitimate ones. Here are some common characteristics found in malicious emails:
- Sender that is out of the ordinary
- Attachments and files that are unexpected or unsolicited
- Offers or requests that seem too good to be true
- Spelling and grammar that are not up to par
- Requests that are urgent or threatening, with a sense of urgency
- Messages that are not personalized
Typical actions frequently requested in phishing emails
In order to carry out their malicious intentions, attackers manipulate victims into performing harmful actions, ranging from disclosing login credentials to downloading a contaminated file. Here are some common actions that are often found in phishing emails:. We will showcase these in our examples of phishing emails.
- Please provide or verify personal information such as your Social Security number, passport, or any other necessary documents.
- Kindly share personal or corporate credit card details if required.
- Feel free to connect with me on LinkedIn or any other social media platform.
- If you receive any unsolicited emails regarding password resets, please ignore them.
Identifying Phishing Emails